Hi ! Here is my write up for the Riverside challenge of the Boston Key Party 2015. It was labeled as a “School Bus” challenge which was a sort of the misc category.
The description of the challenge was:
omg tha NSA hacked my super secret login, I caught them exfillin this pcap, am I t3h fuxxed? : 200
And we were given a 1.5M pcap file. A quick inspection of this capture with wireshark gives us the matter. It is a capture of the USB traffic between one host and some devices.
The first part consists in status and description exchanges between the devices and the host.
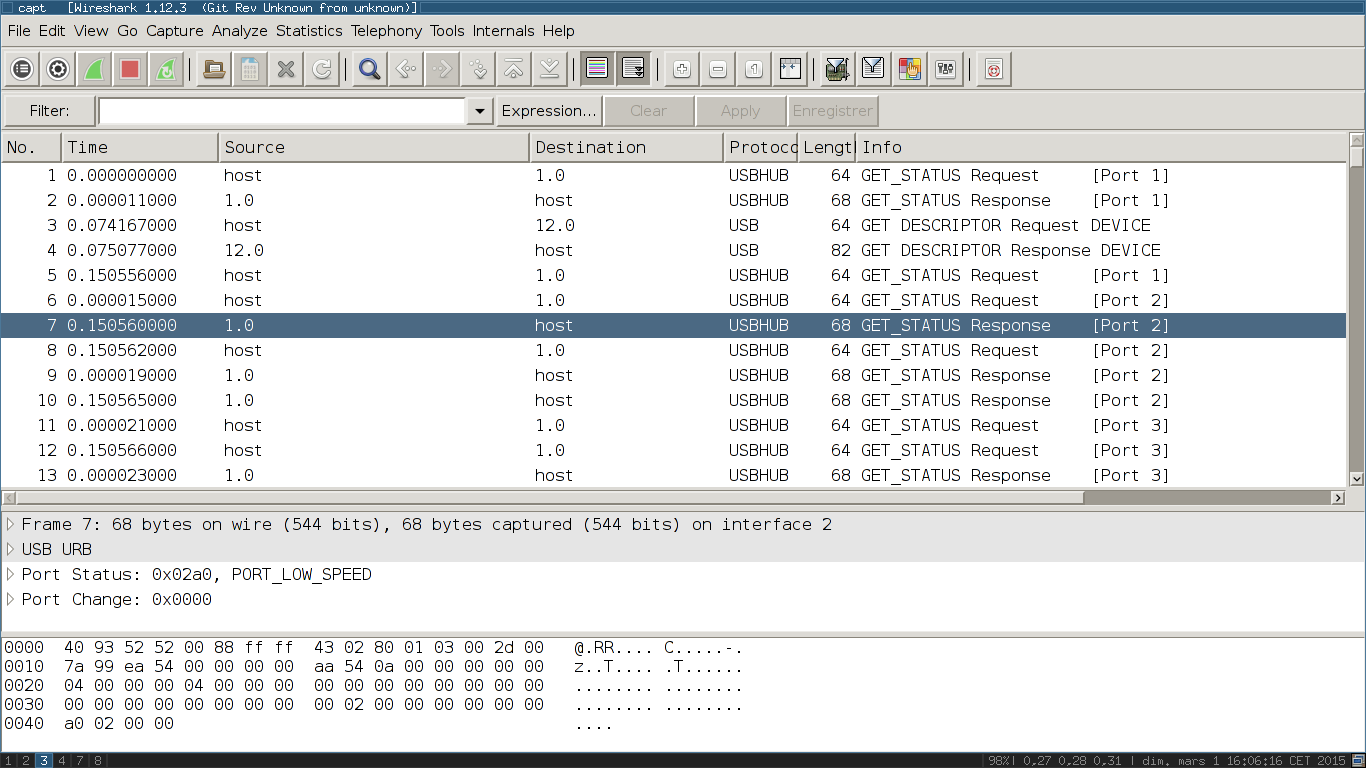
Whereas the second part is only about the device 12 sending ‘URB_INTERRUPT in’ packets to the host and the host’s acknowledgments.
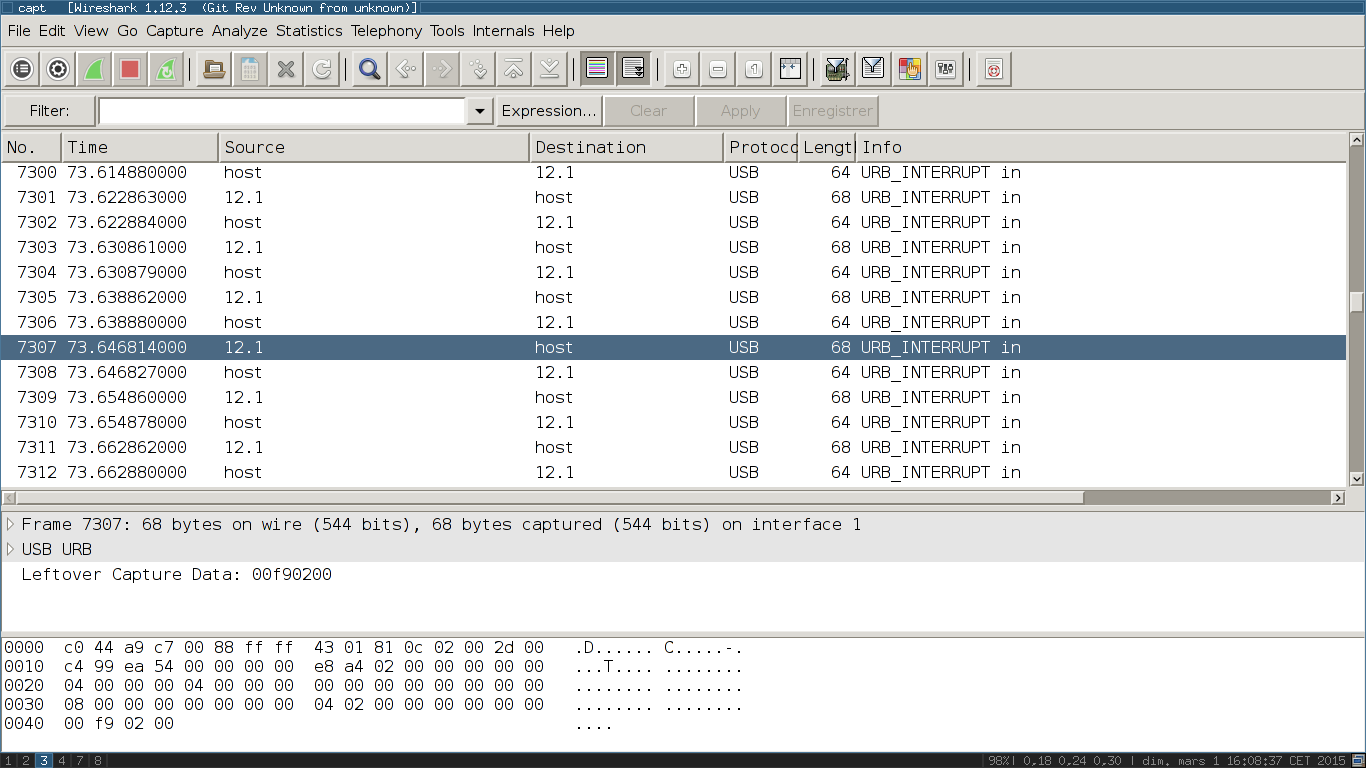
We have around 7600 packets of this kind, they have been sent pretty constantly, with a resolution around the millisecond. They are always carrying 4 bytes of data.
Given the fact the capture is mainly constituted by those packets, I assumed that this is where we should look for the flag.
So, what is the information exchanged in those messages? Well, a packet at the beginning of the file give us a hint, it’s probably a USB mouse.
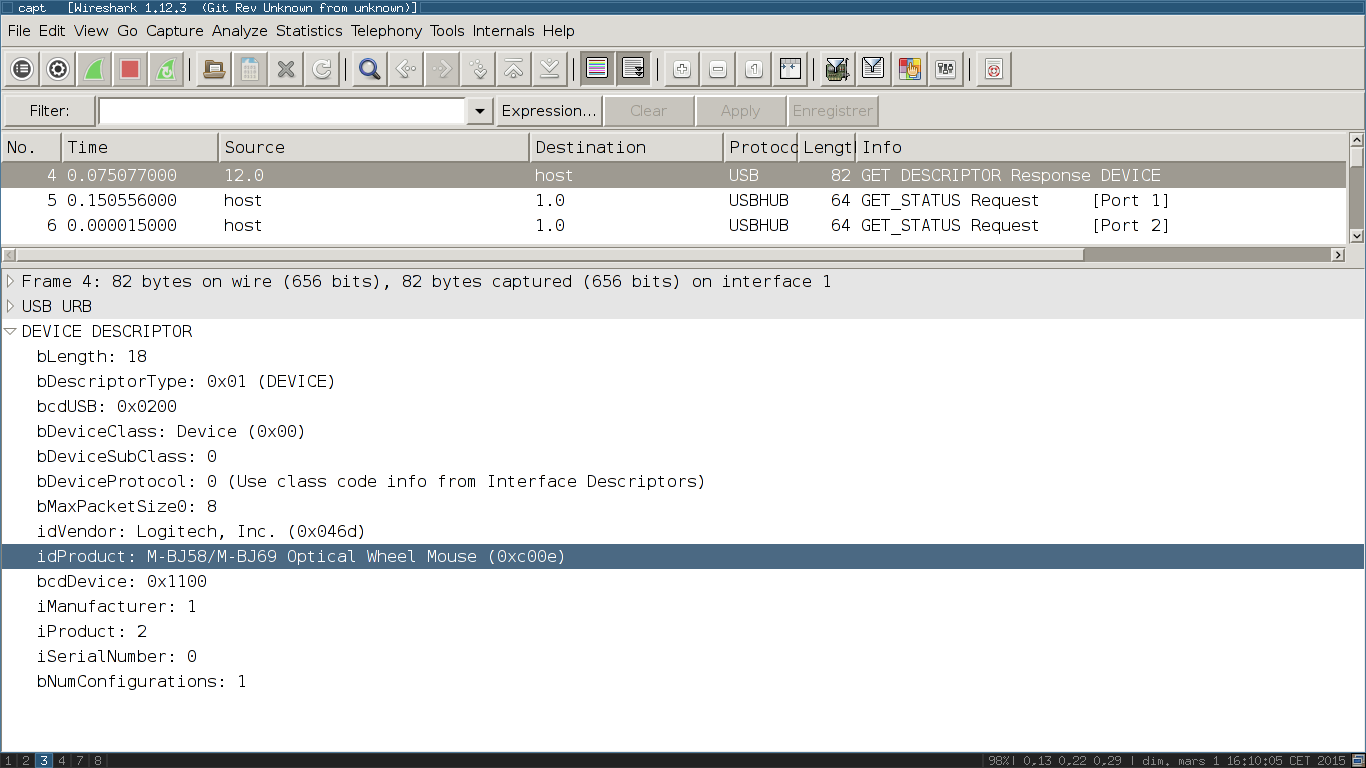
Moreover, according to, link, the data format and values of the packets may match a real mouse exchange:
The second and third bytes are changing every time.
The fourth byte is always null.
But, the first byte doesn’t really match the formats I have found on the internet…
After an analysis of some USB traffic captures of my mouse, here is the format of the data:
[BYTE 1] [?][?][?][?][?][?][?][L]
[BYTE 2] [ MX ]
[BYTE 2] [ MY ]
[BYTE 4] [ NOT USED HERE ]
MX : The horizontal movement in two's complement interpretation
MY : The vertical movement in two's complement interpretation
L : 1 if the left click is pressed
Now, this format seems to completely correspond to the data of the packets!
Let’s export the capture as plain text, parse it and draw the mouse movement with Turtle and Python :)
After a lot of fails, here are the results :
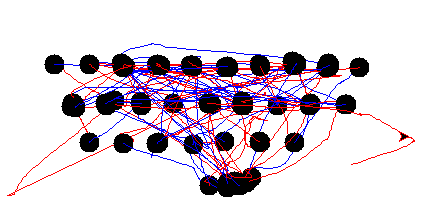
The black dots correspond to the left clicks, and I have changed the pen color between the clicks.
Do you notice the familiar pattern?
Here is the same version with an image in the background to help :)
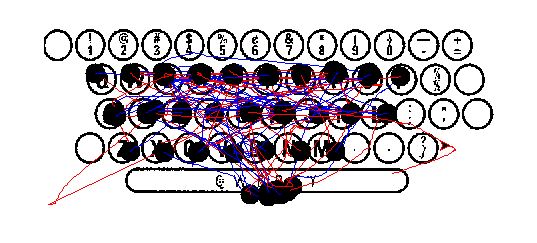
In fact, the user was typing something with his mouse over a typewriter layout.
To get the flag, you just have to follow the Turtle on the keyboard while it is drawing :)
You get : “the quick brown fox jumps over the lazy dog the keyisiheardyoulikedsketchyetchinglastyear”
Thanks to the BKP team ! This was a funny chall’ !
Comments !